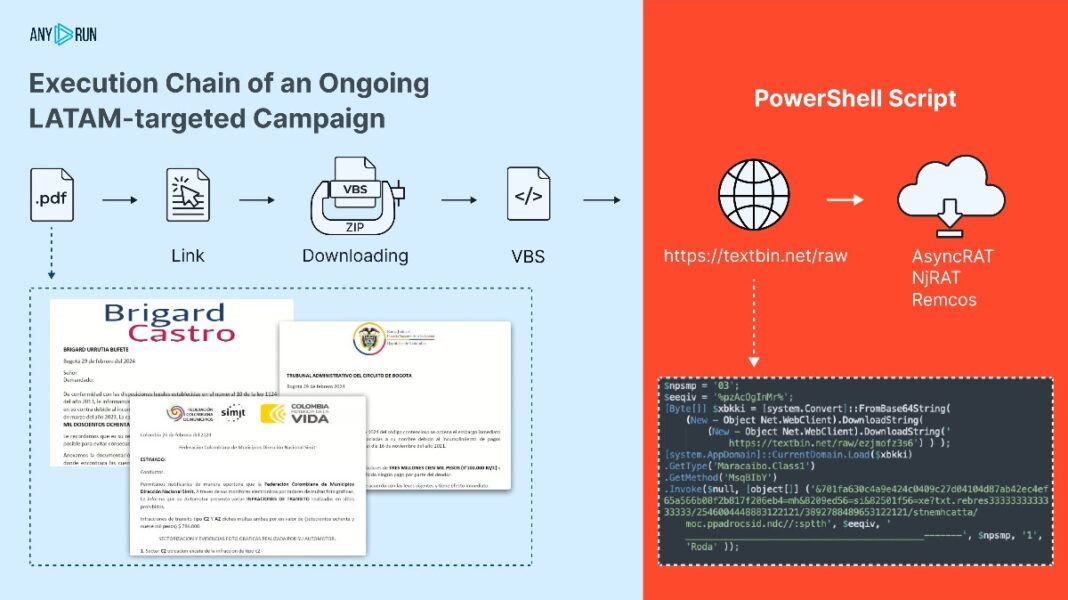
Bad actors impersonating Colombian government agencies are targeting individuals in Latin America. The campaign, as reported by ANY.RUN (@anyrun_app) on Twitter, involves sending phishing emails with PDF attachments accusing recipients of traffic violations or other legal issues. These emails are carefully crafted to appear as though they originate from legitimate government sources, complete with official logos, language, and formatting. The allegations of various legal infractions create a sense of urgency, prompting recipients to take immediate action.
As any well-designed phishing email would do, the deceptive communication is designed to look like a legitimate email, making it easier for unsuspecting victims to download the attachment harbouring a VBS dodgy script. This script initiates a multi-stage infestation process.
When opened, the hidden VBS script activates a PowerShell script, which then fetches the malware from genuine online storage services using a two-step request method.
Uncovering the Infection
The ANY.RUN report, disclosed to GBHackers on Security, outlines the process: the script initially retrieves the malware’s address from sites such as textbin.net. Subsequently, it proceeds to download and execute the malware from this address, which may be hosted on platforms like cdn.discordapp(.)com, pasteio(.)com, hidrive.ionos.com, and wtools.io.
The attackers’ process starts with the PDF, then moves to a ZIP file, followed by VBS and PowerShell scripts, and ends with an executable (EXE) file.
This final payload is one of several remote access trojans (RATs), such as AsyncRAT, njRAT, or Remcos, known for granting unauthorised remote access to infected systems.
These RATs are infamous for posing serious threats to victims’ privacy and data security.
Sample Investigation
The samples from this campaign can be found on ANY.RUN:
Global Impact
The technique exhibited by the attackers in this campaign transcends Latin American targets and could potentially be adapted for use against various targets in different regions.