A sponsored Facebook advertisement using the name Rawiri Wharepapa with a photo of a real Samoan couple has revealed a large-scale scam targeting vulnerable users in New Zealand and the Pacific. This is not a story of loss and luck.
It is a fabricated post, designed using stolen images and text generated to mimic emotional hardship and sudden success.
The purpose is to get clicks, scare users into thinking their devices are infected, and profit from those reactions.
The advertisement opens with a fabricated tragedy involving the sudden death of a wife, a father struggling to raise children, and a miracle discovery of an online casino app that turns his last twenty dollars into nearly one hundred thousand.
Every element of the story is fake. The photos were taken from the real Instagram and Facebook accounts of a couple who have no connection to the scam. The text follows patterns common to scam operations. It switches tone abruptly, uses emojis to play with emotion, and ends with a push to click a link.

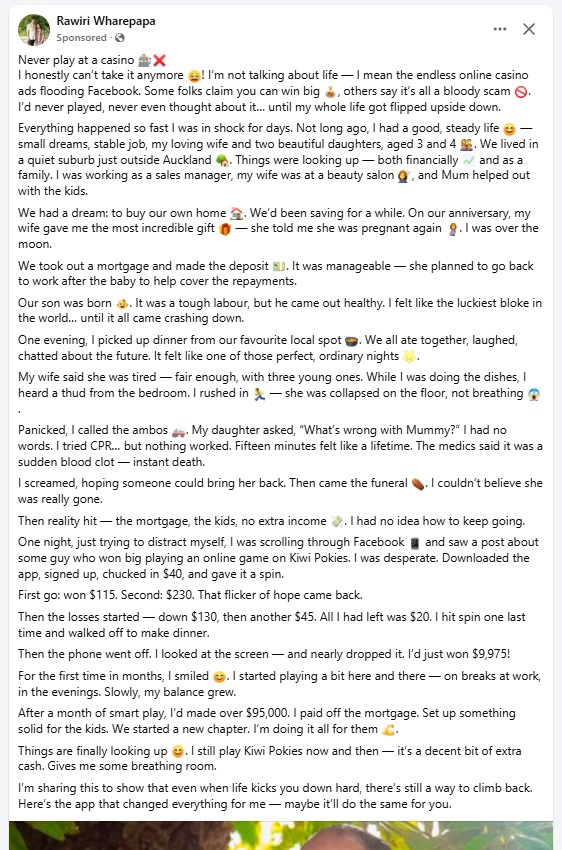
The Samoan couple shown in this fake casino advertisement had their image stolen from their personal accounts. The scammers pulled the photo from public posts on Instagram and Facebook. The real couple has no connection to the ad or the story. Their profiles can be verified at instagram.com/manufouanoai and facebook.com/manufou.
The link behind the ad is not safe. It first loads through Facebook’s own redirect system and then forwards to a domain named sweetpokies.click (Don’t try and open this). The site appears clean when scanned by antivirus platforms because it does not directly serve malware. Instead, it acts as a redirector. When accessed, it forwards users based on location or browser type to another domain such as m4axv8so7.online.
This page is built to trigger a fake antivirus warning using the McAfee brand. It tries to convince the user their device is infected and then asks for permission to send browser notifications or urges them to download a file.

This is the final destination after clicking the scam link. The domain m4axv8fso7.online displays a fake McAfee antivirus warning, claiming the user’s device is infected. It urges the user to run a “quick scan” or enable browser notifications, both tactics designed to scare users into handing over control or clicking further into the scam funnel. This type of popup is known as scareware.
At no point is there a real app. There is no real prize, no winnings, and no secure process. The scam is structured to create panic, lead people into accepting push notifications, and eventually cause them to install malware, give up their data, or click on high-value ads that generate money for the operators.
The comments on the Facebook ad are also part of the trick.
They show names and faces claiming to have won money, purchased phones, or paid off debt. Many include photos of cash or products. But the profiles behind the comments are fake. Most are new, empty, or suspicious. They are used to build trust by showing activity under the scam post, making it appear popular and successful.
We performed a domain lookup of sweetpokies.click. The domain was registered in late September 2024 through joker.com and is masked behind Cloudflare. The registration shows Uganda as the listed country. The domain does not contain any actual content. It is used only to redirect traffic into scareware or affiliate links.
What makes this scam worse is how easily it was constructed using someone’s public profile. The couple’s images were taken from their real accounts. They had posted family pictures, outings, and smiles online — all of it accessible. This was enough for scammers to extract one photo, paste it into their funnel, and run a sponsored ad impersonating the man. This is the result of people uploading their entire lives without restriction. It becomes raw material for exploitation.
We also found the fake Facebook page pretending to be Rawiri Wharepapa.






Fake comments under the scam post create the illusion of community feedback and success. Most of these profiles are new or inactive, typical of comment bots or paid engagement farms.
It has only a few posts, no organic activity, and links to a non-functioning beauty salon website. The same photo of the couple is reused as the profile and cover photo. We compared this to the real Facebook and Instagram accounts belonging to the couple. These authentic profiles show long histories, consistent family activity, verified links, and public recognition. The difference is clear.
This scam runs on speed and volume.
Once an identity is used and reported, they move on to the next. It is designed to trick new users fast and get paid before takedowns occur. The redirect link uses tracking IDs to measure every click. The final site is disposable. The damage is psychological and financial. Users believe they are infected, try to fix it, and end up compromised.
This is not a warning about gambling apps.
It is a warning about how quickly your identity or your family’s images can be pulled from the internet, embedded in a lie, and used in a scam that targets others like you. This is also about how platforms like Facebook continue to allow sponsored ads with little review and how easily those ads reach vulnerable communities.
We have all the screenshots to prove the funnel. We captured the ad, the fake profile, the redirect chain, the scam popup, the comment activity, the WHOIS data showing the scam domain was registered through joker.com and hosted behind Cloudflare with a registrant address in Uganda, and the real couple’s social media accounts. These images will be included in the published article as direct visual evidence.
Do not trust sponsored posts selling emotional stories with quick fixes.
Do not allow browser notifications from unfamiliar domains. Do not assume that just because it is on Facebook, it is safe. And if you share your life publicly, make sure you understand what someone else could do with it.
This scam was built to monetise stolen trust. Now it’s been broken down for all to see.





